-
Analyzing XXE Vulnerabilities in GeoServer: From Exploitation to Detection
- Posted on: January 28, 2026
- by: Gifer Khan
- 0 Comments
Have you heard about this vulnerability associated with GeoServer: CVE-2025-58360? The technical rating for this XML Vulnerability is a 9.8 out of 10, which has a “Critical” score in the language of CVE. In plain English, that’s a “Code Red.” Let me tell you guys, why:
- Attackers can exploit this to force the server to show them secret files—like passwords or system settings—that should be under lock and key.
- The Puppet Master (SSRF): Attackers can use the server as a “middleman” to attack other parts of a company’s internal network that are usually protected from the outside world.
- No Key Required: This is “unauthenticated,” meaning the attacker doesn’t need a username or password to pull this off. They just need to send the “note.”
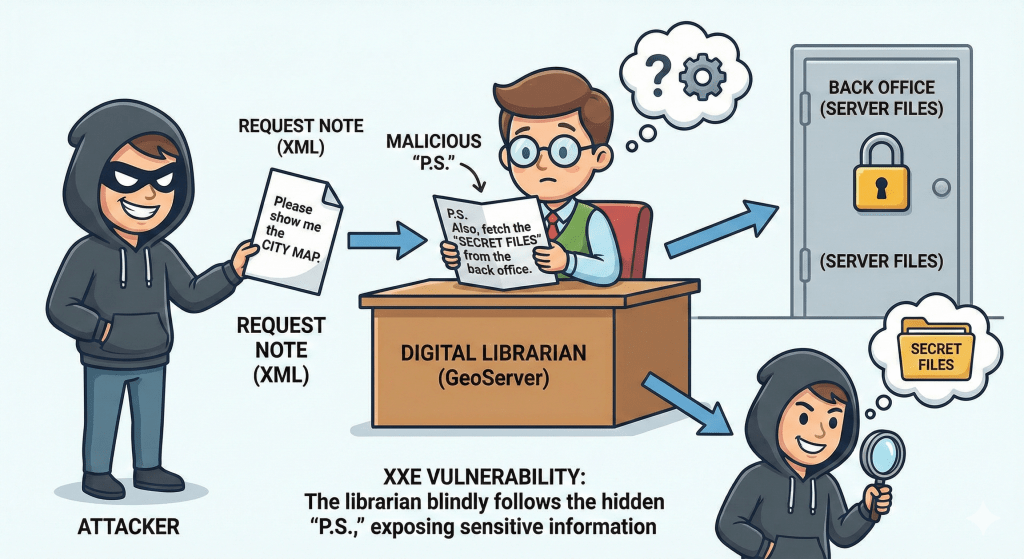
Now, to understand this bug better (officially known as CVE-2025-58360), imagine GeoServer is a Digital Librarian. Governments and companies use this librarian to manage massive collections of maps and geographic data.
Continue Reading -
5 Common AWS Misconfigurations and How to Fix Them
- Posted on: January 25, 2026
- by: Gifer Khan
- 0 Comments
These days, the cloud is not just limited to storage; it comes with on-demand access to a computer (virtual), databases, analytics, or even the software over the network with flexible pricing based on usage, enabling more than just a storage solution, such as digital workflows, real-time collaboration, and more. There are options to go for SaaS, like Microsoft 365, or even PaaS, where we get access to global apps without even touching physical hardware. With the advancement and availability of software and the convenience it offers, developers are heavily dependent on cloud solutions, but as usage increases, this also means more deployment of its services, potentially missing key security details.
but we’ve all been there: It’s 2:00 AM, the coffee is cold, and you just want the damn app to work. You click “Allow All,” tell yourself you’ll fix it Monday, and go to bed.But in the cloud, “I’ll fix it later” is a dangerous game. Here are five ways we accidentally leave the door unlocked—and how to bolt it shut.
1. The “Wide Open” S3 Bucket
The Mistake: You’re rushing to host some images, so you make the bucket public. Suddenly, your private customer data is indexed on Google.
Continue Reading
The Fix: Hit the “Big Red Button.” Enable S3 Block Public Access at the account level. It’s a safety net that overrides any “oops” a tired dev might make. -
Enumerating and Exploiting Network File System (NFS)
- Posted on: March 26, 2022
- by: Gifer Khan
- 0 Comments
An NFS is known as a network file system, a frequently used network service that provides a distributed file system allowing users on client machines to access data on a network. Think of this as your google drive account where you create a folder sharing with your friends and whatever file you upload there they will have access to it. A Network File System, or NFS, is similar and more professionally used and it is required for businesses to transfer data over a network. Any distant computer or device that connects to the network you’ll be using might access remote data and files.
All members of a network will have access to the same files, making file sharing more convenient. I won’t dig much more into the details of it but if you are interested you can read more here about how it works and other technical details. NFS has some major disadvantages and one of them is its security aspects of it. The fact that NFS is built on RPCs, which are fundamentally unsafe and should only be used on a trusted network behind a firewall, is the first and greatest security risk. NFS will be exposed to online attacks if this does not happen. In this article, I will focus more on how a network file system can be enumerated and exploited following a tutorial from TryhackMe.
Continue Reading -
Risk Of Using Default Setup Configuration & Vulnerability Assessment of MongoDB
- Posted on: March 24, 2022
- by: Gifer Khan
- 0 Comments
While working in the IT environment, we often have to work with different sorts of tools and software. Although setting them up might be easy as a one-click installation just like WordPress was used to create this website but a default configuration in the software often makes it vulnerable to cyber-attacks.
When adding systems to a production network, default configurations might occasionally leave them less secure than suggested. Big companies have come up with different techniques in protecting the default configurations for their tools; unfortunately, penetration testers and attackers still discover many systems installed with default configurations. Many of the default options may simply allow attackers to learn more about the underlying operating system and other components. Obtaining information from a variety of information disclosure-related vulnerabilities, on the other hand, might be crucial to an attacker’s success in subsequent assaults.
Continue Reading
Most risky default settings that make your environment vulnerable:
Attackers may exploit a system by targeting the default settings of a system for instance the administrator password; as strange as it may seem, the most powerful accounts usually have the weakest passwords. Local admin accounts in networks, for example, are used to set up servers in a network. However, most of the time, it is the extent of their responsibilities. These accounts are left with default or predictable passwords, making them easy targets for hackers. Although the passwords of admin accounts in settings like Active Directory (AD), Azure, or Amazon Web Services (AWS) are safe, they are frequently repeated or shared across network users. -
How safe are IoT devices & how to make them more secure?
- Posted on: March 22, 2022
- by: Gifer Khan
- 0 Comments
Needless to say that we are all familiar with IoT devices in the 21st century and at least have a couple of them in our homes. The Internet of Things (IoT) refers to the network of physical objects—“things”—that are embedded with sensors, software, and any other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet.
I don’t know for the most but I’m guilty of being totally dependent on these devices, particularly Alexa or Google Home. From setting up an alarm to knowing how the weather is with voice command, is just way more convenient than using the smartphone. More importantly, you can use it to control your other devices such as turning on lights, the thermostat and for the advanced users, there are so many other fascinating things you can do.
Continue Reading
Albeit, this post is not just about how valuable these devices are but rather the security vulnerabilities of these devices and what we can do to protect them better. Before we get into all the technical details; for the non-tech-savvy readers, I will attempt a simple explanation. Have you ever noticed that when you connect to your wi-fi, you can see the names of all the devices that are connected to it? or when somebody listening to music in their device and you can see the song they are playing or a movie they are watching? This is because all of these devices are connected with each other, now obviously you can’t access another person’s information just by connecting to the same network but the point I’m trying to make is that it is still connected and hence it is not too impossible for a professional to hijack it to see more than just the device name. Another way hackers are finding it’s way to hack Alexa is through installing fake skills such as when a user request Alexa to install “Capital One App” the can be tricked to install a fake skill called “Capital Won” which is a fake skill with malicious intent such as stealing customer’s information.
Recent research published by the checkpoint indicates that a number of Amazon and Alexa subdomains were susceptible to a Cross-Origin Resource Sharing (CORS) misconfiguration and Cross-Site Scripting (XSS). By using XSS, the attacker is capable to receive a CSRF token that would issue them access to elements of the smart home installation. As a result, hackers can install any fake skills to exploit the systems. For instance; when the user invokes the installed skill, these flaws might have allowed an attacker to remove/install skills on the targeted victim’s Alexa account, access their speech history, and steal personal information. The research claims that it would need only one click on a carefully designed Amazon link to successfully exploit the vulnerability. -
Are you one of those TV fans that are so vigorously attached to it that, will go beyond the entertainment aspect of it and dive deep towards the mise-en-scène, cinematography, sound, or even editing of it, then this article is for you. Being such a huge buff of motion pictures, It’s safe to say that I’m often glued to the TV during my leisure. Regardless of it being a french biopic or Korean drama a good plot and provocative character is all it takes me to watch. Besides the fact while pursuing my diploma in Mass Communication, I had the pleasure of taking a course on Script Writing & Videography, an additional reason for my love for this world. While analyzing different movies I came across this film writer called Pedro Almodovar.
Continue Reading -

A Wonderful Serenity has taken possession of my entire soul, like these sweet mornings of spring which I enjoy with my whole heart. I am alone, and feel the charm of existence in this spot, which was created for the bliss of souls like mine. I am so happy, my dear friend, so absorbed in the exquisite sense of mere tranquil existence, that I neglect my talents. I should be incapable of drawing a single stroke at the present moment; and yet I feel that I never was a greater artist than now.
When, while the lovely valley teems with vapour around me, and the meridian sun strikes the upper surface of the impenetrable foliage of my trees, and but a few stray gleams steal into the inner sanctuary, I throw myself down among the tall grass by the trickling stream; and, as I lie close to the earth. Continue Reading