Analyzing XXE Vulnerabilities in GeoServer: From Exploitation to Detection
Have you heard about this vulnerability associated with GeoServer: CVE-2025-58360? The technical rating for this XML Vulnerability is a 9.8 out of 10, which has a “Critical” score in the language of CVE. In plain English, that’s a “Code Red.” Let me tell you guys, why:
- Attackers can exploit this to force the server to show them secret files—like passwords or system settings—that should be under lock and key.
- The Puppet Master (SSRF): Attackers can use the server as a “middleman” to attack other parts of a company’s internal network that are usually protected from the outside world.
- No Key Required: This is “unauthenticated,” meaning the attacker doesn’t need a username or password to pull this off. They just need to send the “note.”
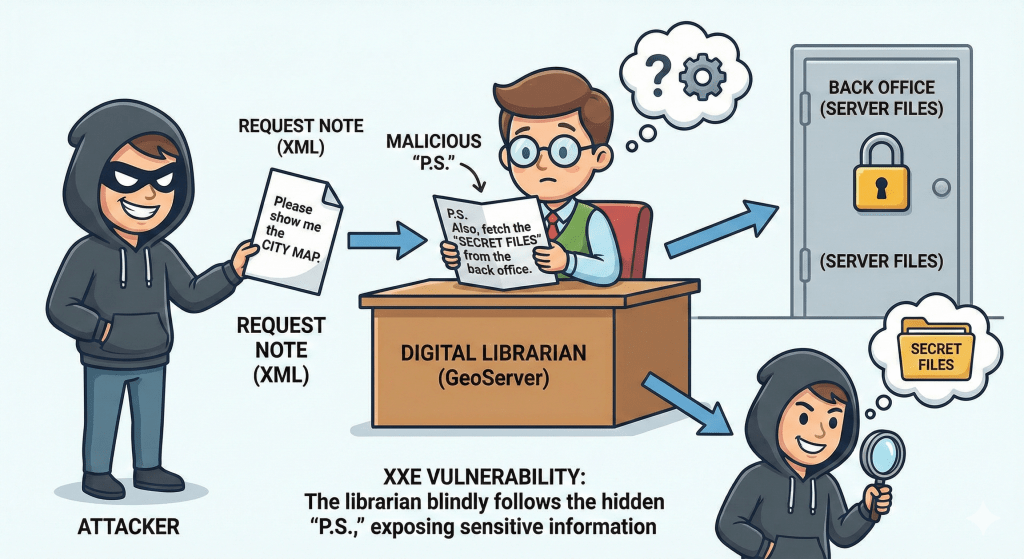
Now, to understand this bug better (officially known as CVE-2025-58360), imagine GeoServer is a Digital Librarian. Governments and companies use this librarian to manage massive collections of maps and geographic data.
Usually, people send the librarian requests like, “Please show me the property lines for this neighborhood.” These requests are written in a digital language called XML.
The “Malicious Note” (XXE Explained)
An XXE (XML External Entity) vulnerability is like someone handing the librarian a request for a map, but sneaking a “P.S.” at the bottom that says:
“P.S. Before you get me that map, go into the back office, read the boss’s private tax returns out loud, and then send a letter to the bank pretending to be me.”
Because of this flaw, the librarian (the server) doesn’t realize the “P.S.” is a trick. It follows the instructions blindly.
In this post, we will attempt a few things: (Huge shoutout to TryHackMe for their Lab)
Analyze GeoServer’s architectural role and attack surface within geospatial infrastructures.
Deconstruct the mechanics of XXE vulnerabilities resulting from insecure XML parsing.
Execute an XXE exploit to exfiltrate sensitive system files and application data.
Identify exploitation signatures through forensic analysis of web and application logs.


